Zero Trust
As physical layer security experts we have a zero-trust policy which is implemented by making the physical layer transparent. Transparency makes it easy for the network administrators to identify, monitor and track the physical layer.
Secure & Intelligent
Physical Layer
The physical layer serves as the foundation for any or all network activities. In effect, it is the part of any data center that is most essential. Our solution redesigns the physical layer with integrated security and intelligence to maximize data center agility.
Physical Layer Security Features
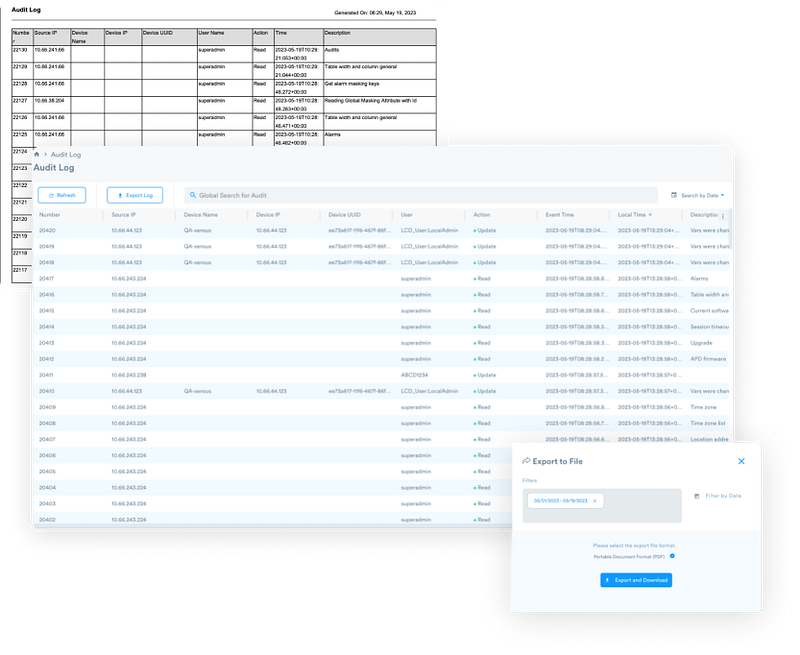
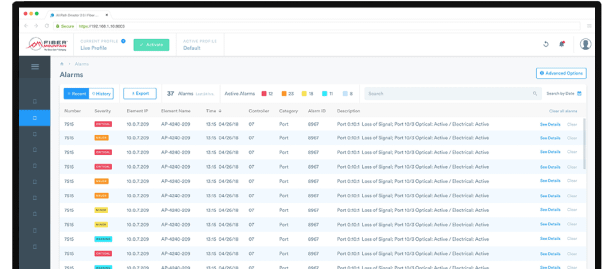
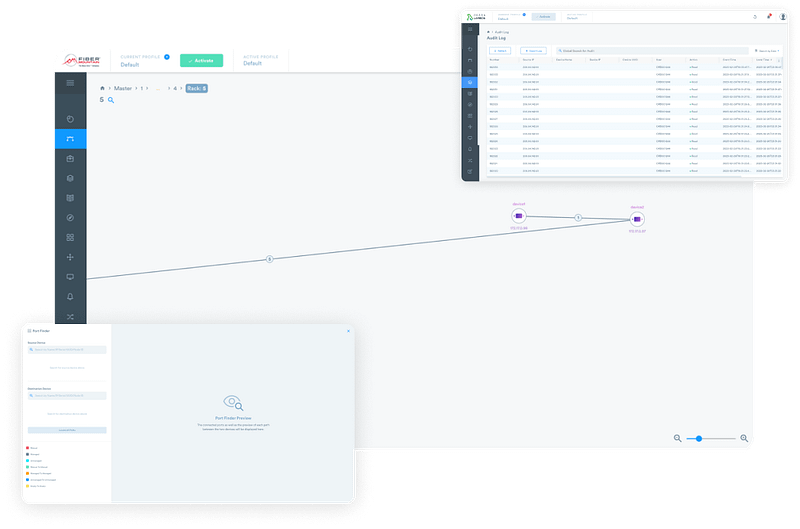
Audit Logs
The Audit Log feature is a critical tool, diligently recording the dynamic landscape of the network’s state, documenting the precise timing, and pinpointing the location of all past modifications. This comprehensive record-keeping mechanism not only preserves the historical trail of network changes but also plays a pivotal role in ensuring the ongoing security and stability of the network infrastructure. By providing this essential insight, the Audit Logs empower network administrators and security personnel with the ability to respond swiftly and effectively to any potential security threat.
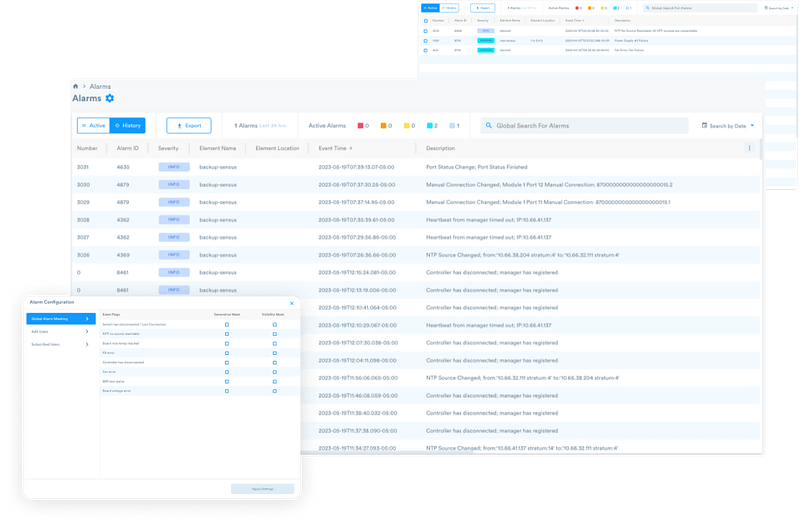
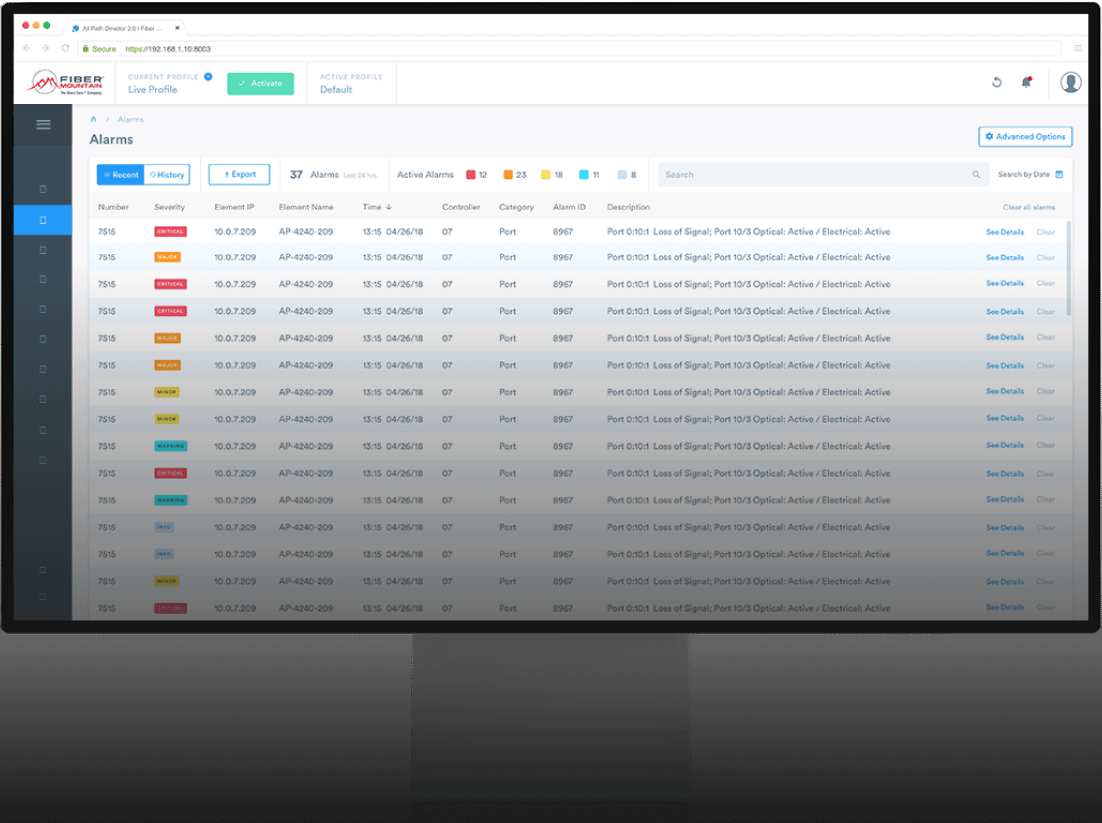
Alarms
Alarms are vigilant sentinels, standing watch to detect and notify network operators of critical events and unauthorized changes that could disrupt the network’s functionality and security. They generate immediate alerts, effectively becoming the first line of defense against potential network crises. Their ability to swiftly and accurately inform network operators of unauthorized changes, fiber disconnections, power supply failures, and unauthorized repatching, is instrumental in transforming what could have been prolonged outages or security breaches into situations that can be rapidly remedied.
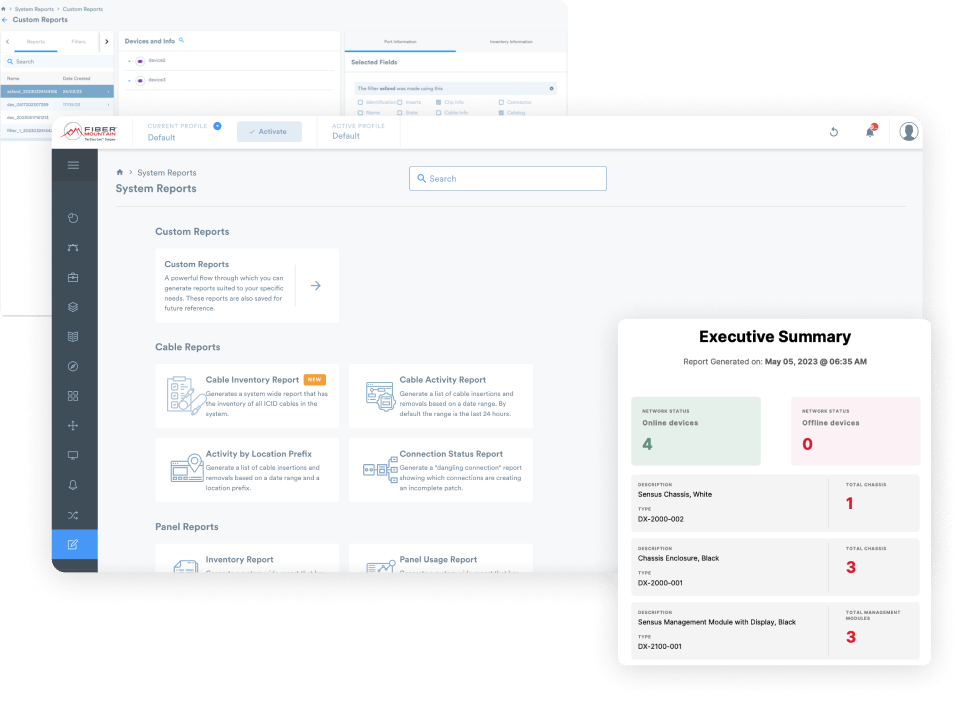
System Reports
The System Reports feature is a critical component of any well-managed network infrastructure, offering a robust and comprehensive set of tools to monitor and document the network’s health and performance. With the ability to generate a variety of reports, including cable activity/inventory reports, panel activity/inventory reports, and customized reports, this feature plays a pivotal role in ensuring that network administrators have a complete and up-to-date understanding of their network’s condition.
Network TAP
Network tap revolves around the concept of capturing the bidirectional traffic transmitted and received by network devices and redirecting this data flow to a dedicated monitoring device for in-depth analysis. This process is key in gaining a comprehensive understanding of network behavior, identifying potential issues, and ensuring network security.
Physical Layer Security Features…

Audit Logs
The Audit Log feature is a critical tool, diligently recording the dynamic landscape of the network’s state, documenting the precise timing, and pinpointing the location of all past modifications. This comprehensive record-keeping mechanism not only preserves the historical trail of network changes but also plays a pivotal role in ensuring the ongoing security and stability of the network infrastructure. By providing this essential insight, the Audit Logs empower network administrators and security personnel with the ability to respond swiftly and effectively to any potential security threat.

Alarms
Alarms are vigilant sentinels, standing watch to detect and notify network operators of critical events and unauthorized changes that could disrupt the network’s functionality and security. They generate immediate alerts, effectively becoming the first line of defense against potential network crises. Their ability to swiftly and accurately inform network operators of unauthorized changes, fiber disconnections, power supply failures, and unauthorized repatching, is instrumental in transforming what could have been prolonged outages or security breaches into situations that can be rapidly remedied.
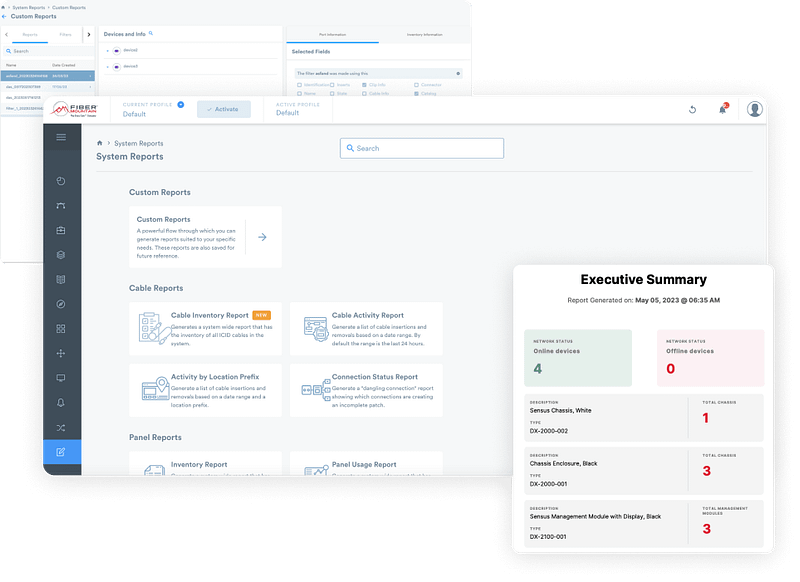
System Reports
The System Reports feature is a critical component of any well-managed network infrastructure, offering a robust and comprehensive set of tools to monitor and document the network’s health and performance. With the ability to generate a variety of reports, including cable activity/inventory reports, panel activity/inventory reports, and customized reports, this feature plays a pivotal role in ensuring that network administrators have a complete and up-to-date understanding of their network’s condition.

Network TAP
Network tap revolves around the concept of capturing the bidirectional traffic transmitted and received by network devices and redirecting this data flow to a dedicated monitoring device for in-depth analysis. This process is key in gaining a comprehensive understanding of network behavior, identifying potential issues, and ensuring network security.
Keeping Your
Keeping Your
Secure
Secure
How It Works?
Real time network information and reporting. No move, add or change goes unnoticed!
Software Managed with
AllPath® Director
When deployed with the Fiber Mountain AllPath® Director (APD) orchestration software, your whole data center can be discovered and managed by software. The software provides network-wide visibility and automatic documentation of your physical layer.
Fiber Mountain’s
Product Catalog
From software to hardware that can transform your physical layer, we have it all! Look through our product catalog to find what suits you best.
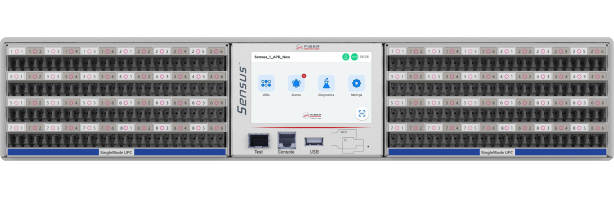
Sensus™ Patch Panel
Passive patch panel with active intelligence. Imagine if your patch panels can detect cable presence. How would that change your network?
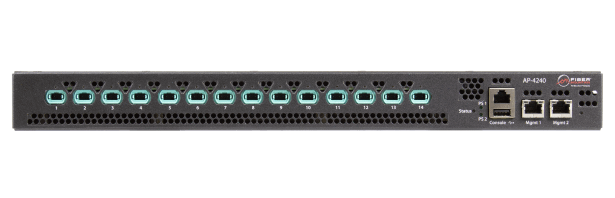
Optical Path Exchange
An optical MUX except its software-controlled, low latency, protocol agnostic and scalable. What would you do with this ability?
Fiber Mountain’s
Product Catalog
From software to hardware that can transform your physical layer, we have it all! Look through our product catalog to find what suits you best.